Splunk
Understanding Splunk's Data Platform and Core Features
Splunk stands as a leading platform for searching, monitoring, and analyzing machine-generated big data through a web-style interface. The platform ingests and indexes massive amounts of data from any source, making it searchable and actionable. Security teams, IT operations, and business analysts rely on Splunk to gain real-time visibility into their digital systems.
The platform excels at real-time data processing, offering powerful search capabilities across diverse data sources. Its core strengths include customizable dashboards, advanced analytics tools, and extensive integration options. Splunk's architecture supports massive scalability, allowing organizations to process petabytes of data while maintaining fast search performance.

Benefits of AI Agents for Splunk
What would have been used before AI Agents?
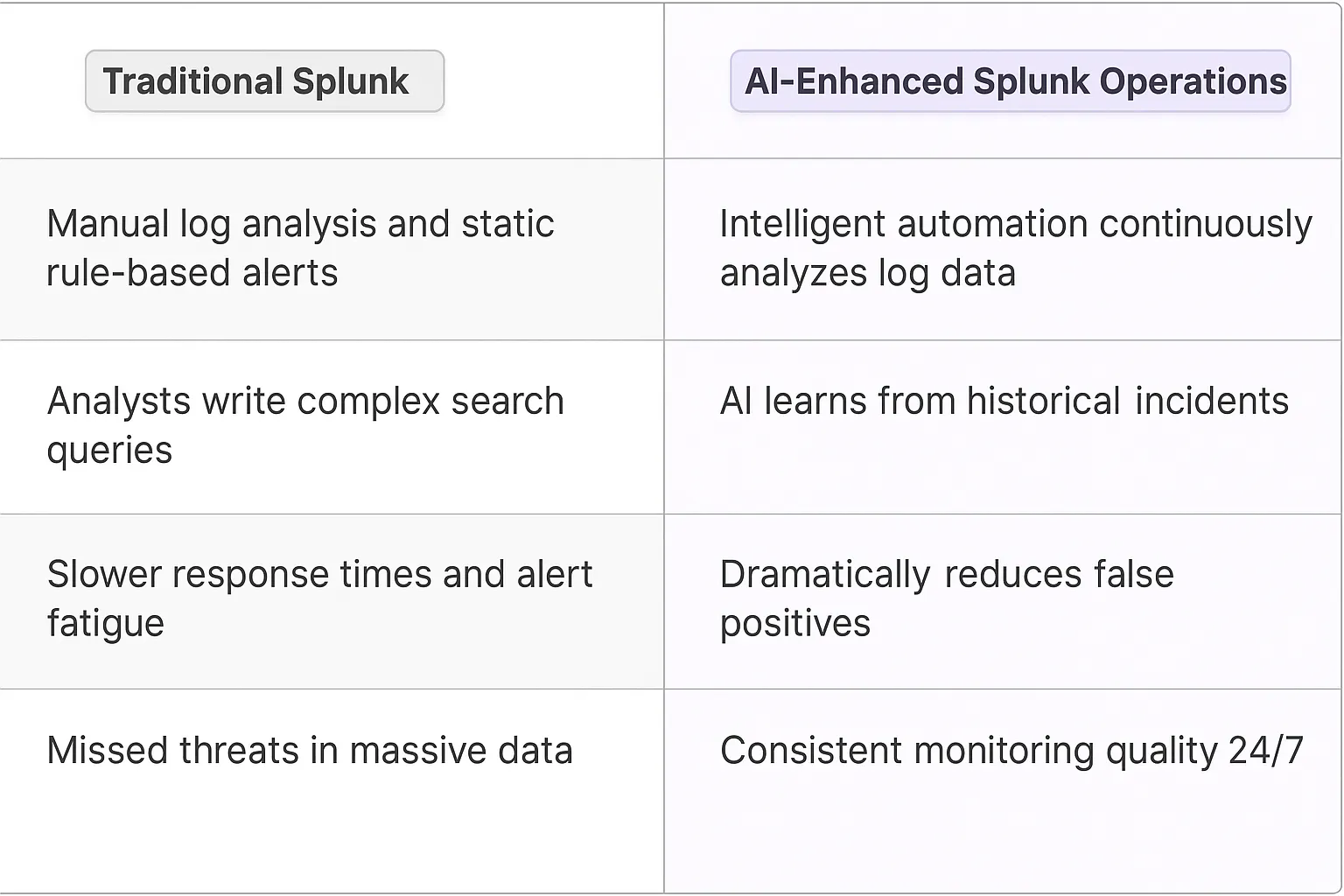
Security teams traditionally relied on manual log analysis and static rule-based alerts in Splunk. Analysts spent countless hours writing complex search queries, creating correlation rules, and investigating each security incident individually. This meant slower response times, alert fatigue from false positives, and missed threats due to human limitations in processing massive amounts of security data.
What are the benefits of AI Agents?
AI Agents transform Splunk's security operations by bringing intelligent automation to threat detection and response. These digital teammates continuously analyze log data, identifying subtle patterns and anomalies that human analysts might miss.
The most significant advantage comes from the agents' ability to learn from historical security incidents. They develop an understanding of normal vs. suspicious behavior specific to each organization's environment. This contextual awareness dramatically reduces false positives while catching sophisticated attacks that traditional rules would miss.
When investigating incidents, AI Agents can simultaneously analyze multiple data sources - correlating logs across network traffic, endpoint activities, and user behaviors. They automatically enrich alerts with relevant context, saving analysts precious investigation time.
For SecOps teams running 24/7 operations, AI Agents serve as tireless digital teammates that never need breaks. They maintain consistent monitoring quality at all hours, addressing the chronic challenge of alert fatigue and analyst burnout.
The force multiplier effect is particularly powerful in resource-constrained security teams. AI Agents handle routine analysis tasks, freeing up human analysts to focus on strategic security initiatives and complex investigations that require creative problem-solving.
Most importantly, these agents continuously improve their detection capabilities through machine learning, adapting to new threats and attack patterns as they emerge. This creates a proactive security posture rather than a reactive one.
Potential Use Cases of AI Agents with Splunk
Security Operations
AI Agents transform security operations by analyzing Splunk's vast log data in real-time. They detect anomalies, investigate potential threats, and provide contextual insights about security incidents. When suspicious patterns emerge, these digital teammates can automatically trigger incident response workflows and generate detailed reports for security teams.
Infrastructure Monitoring
System administrators gain powerful allies in AI Agents that continuously monitor infrastructure health through Splunk. These agents track performance metrics, predict potential system failures, and proactively suggest optimization strategies. They can correlate seemingly unrelated events across different systems to identify root causes of performance issues. Infrastructure Monitoring capabilities are enhanced when AI agents work alongside specialized monitoring tools.
Business Analytics
AI Agents excel at extracting meaningful business insights from Splunk's data repositories. They analyze customer behavior patterns, identify revenue opportunities, and spot market trends. The agents can generate custom dashboards and reports, translating complex data into actionable intelligence for business stakeholders. Business Analytics platforms benefit significantly from this AI-enhanced approach.
Application Performance Management
Development teams benefit from AI Agents that monitor application performance in Splunk. These agents track error rates, response times, and user experience metrics. They identify bottlenecks, debug issues, and recommend specific code-level improvements to enhance application reliability.
Compliance and Audit
AI Agents automate compliance monitoring by continuously scanning Splunk logs for regulatory violations. They maintain audit trails, generate compliance reports, and alert relevant teams about potential policy breaches. This systematic approach reduces manual oversight while ensuring consistent regulatory adherence.
Capacity Planning
AI Agents analyze historical usage patterns in Splunk to forecast resource requirements. They provide data-driven recommendations for infrastructure scaling, helping organizations optimize their resource allocation and prevent service disruptions due to capacity constraints.
Log Analysis and Management
The sheer volume of log data in Splunk becomes manageable with AI Agents that automatically categorize, filter, and prioritize logs. They identify critical events, establish correlations between different log sources, and maintain optimal log retention policies based on data importance and compliance requirements.
These use cases demonstrate how AI Agents enhance Splunk's capabilities across multiple domains, creating more efficient and intelligent operational environments. Organizations can deploy these digital teammates to handle routine tasks while human experts focus on strategic initiatives and complex problem-solving.

Industry Use Cases
The integration of AI agents with Splunk creates powerful new capabilities for organizations wrestling with massive data streams and complex security challenges. These digital teammates excel at parsing through Splunk's extensive log data, identifying patterns, and extracting actionable insights that would take human analysts days or weeks to uncover.
While Splunk's core strengths in log management and security analytics are well-established, AI agents amplify these capabilities across multiple sectors. They operate as tireless data investigators, working alongside security teams and IT operators to transform raw machine data into strategic intelligence.
The real power emerges when these AI agents tap into Splunk's rich ecosystem of data connectors and analytics tools. From financial services firms monitoring transaction anomalies to healthcare providers safeguarding patient records, organizations are discovering innovative ways to deploy these digital teammates within their Splunk environments.
The following industry examples demonstrate how AI agents enhance Splunk's capabilities, creating more resilient and responsive operations across different business contexts. Each case highlights specific challenges where the combination of AI and Splunk's robust platform delivers exceptional value.
Financial Services: AI-Powered Fraud Detection with Splunk
The financial services sector faces an endless stream of sophisticated fraud attempts, with criminals constantly evolving their tactics. Splunk AI Agents transform how banks and financial institutions detect and prevent fraudulent activities by analyzing massive volumes of transaction data in real-time.
When integrated into a bank's security operations center, Splunk AI Agents continuously monitor transaction patterns across multiple channels - from ATM withdrawals to online banking sessions. The AI examines hundreds of data points per transaction, including location, device information, transaction amount, and historical user behavior.
For example, when a customer makes a series of unusual purchases, the AI Agent doesn't just flag the behavior - it provides context by correlating current activities with the customer's typical spending patterns, recent travel data, and known fraud schemes in that geographic region. This deep contextual analysis helps security teams focus on genuine threats while reducing false positives that can frustrate legitimate customers.
The AI Agent also adapts its fraud detection models based on new data and confirmed fraud cases. When security analysts validate or dismiss alerts, the system learns from these decisions to improve its accuracy. This continuous learning loop means the AI becomes increasingly precise at identifying subtle fraud indicators that human analysts might miss.
Beyond just detection, these digital teammates can initiate automated responses - temporarily freezing suspicious transactions, sending risk-based authentication challenges to users, or routing high-risk cases to specialized fraud teams. This rapid response capability helps financial institutions stop fraud attempts before funds leave the system.
The measurable impact is significant: Financial institutions using Splunk AI Agents for fraud detection typically see a 60% reduction in false positives and can identify fraudulent transactions up to 95% faster than traditional rule-based systems. This translates into millions in prevented losses while maintaining a smooth experience for legitimate customers.
Healthcare: Predictive Patient Monitoring Through Splunk AI
Healthcare organizations face immense pressure to detect patient deterioration before it becomes critical. Splunk AI Agents are transforming intensive care units by analyzing thousands of patient vital signs and medical device readings per second to identify subtle warning signs that even experienced clinicians might overlook.
The AI Agent processes multiple data streams simultaneously - from heart monitors, ventilators, medication pumps, and electronic health records. By correlating these diverse inputs, the system spots complex patterns that often precede serious complications. For instance, when monitoring a post-surgical patient, the AI analyzes micro-changes in vital signs, medication responses, and lab results to predict potential complications hours before traditional monitoring systems would raise an alarm.
These digital teammates don't just collect data - they actively learn from patient outcomes. Each time a prediction proves accurate or requires adjustment, the system refines its understanding of risk factors specific to different patient populations and conditions. A hospital in California implemented this system and reduced their cardiac arrest rates by 35% within six months by catching warning signs earlier.
The AI Agent also factors in historical patient data, genetic markers, and population health trends to create personalized risk profiles. When monitoring a diabetic patient with heart disease, the system considers how similar patients responded to treatments, allowing for more precise interventions. This level of personalization helps medical teams move from reactive to proactive care.
Real-world impact metrics show that hospitals using Splunk AI Agents for patient monitoring have achieved a 45% reduction in unexpected ICU transfers and a 28% decrease in length of stay. The system also helps optimize resource allocation by predicting patient flow and staffing needs with 89% accuracy.
Most importantly, these AI Agents serve as a force multiplier for healthcare teams. They handle the continuous monitoring of complex data streams, allowing medical professionals to focus on patient care while remaining confident they won't miss critical changes in patient condition. This partnership between human expertise and AI capabilities is creating a new standard for patient safety and care quality.
Considerations for Splunk AI Implementation
Implementing AI agents within Splunk environments requires careful planning and strategic thinking around several key areas. Organizations need to evaluate their data architecture, security protocols, and operational readiness before deployment.
Technical Challenges
Data quality stands as a primary technical hurdle when deploying AI agents in Splunk. The system requires clean, properly formatted data to function effectively. Many organizations struggle with inconsistent logging formats, missing timestamps, or incomplete field values that can impact AI performance.
Resource allocation presents another significant challenge. AI agents processing large volumes of Splunk data need substantial computational power. Organizations must carefully monitor CPU usage, memory consumption, and storage requirements to prevent system degradation.
Operational Challenges
Team adoption often becomes a critical factor in successful implementation. Security analysts and IT teams need proper training to understand how AI agents interpret and process Splunk data. Without this knowledge foundation, teams may either underutilize the technology or become overly dependent on it.
Alert fatigue remains a persistent concern. While AI agents can process massive amounts of data and generate insights, they may trigger numerous alerts that overwhelm security teams. Finding the right balance between sensitivity and specificity requires ongoing tuning and adjustment.
Integration Considerations
API compatibility affects how smoothly AI agents interact with existing Splunk deployments. Organizations need to verify that their current Splunk version supports the intended AI capabilities and that all necessary APIs are accessible and properly configured.
Custom field extraction and correlation rules may need modification to work effectively with AI agents. Teams should review and update their existing Splunk configurations to ensure optimal performance with the new AI layer.
Governance Requirements
Data privacy regulations impact how AI agents can process and analyze certain types of information. Organizations must establish clear guidelines about what data the AI can access and how it should handle sensitive information.
Audit trails become increasingly important when AI agents make automated decisions. Teams need to implement robust logging mechanisms to track AI actions and maintain compliance with security policies.
Enhanced data processing capabilities require careful consideration of these implementation factors to ensure successful deployment.
The Future of AI-Enhanced Data Analytics
The marriage of AI Agents and Splunk represents a significant leap forward in data analytics and operational intelligence. Organizations across industries are discovering that these digital teammates amplify their existing Splunk investments, enabling deeper insights and faster response times. As AI technology continues to evolve, we'll likely see even more innovative applications emerge, further transforming how organizations leverage their data through Splunk.
Success in this space requires careful attention to implementation details, team training, and governance frameworks. Organizations that thoughtfully deploy AI Agents within their Splunk environments position themselves to handle growing data volumes while maintaining operational efficiency and security effectiveness.